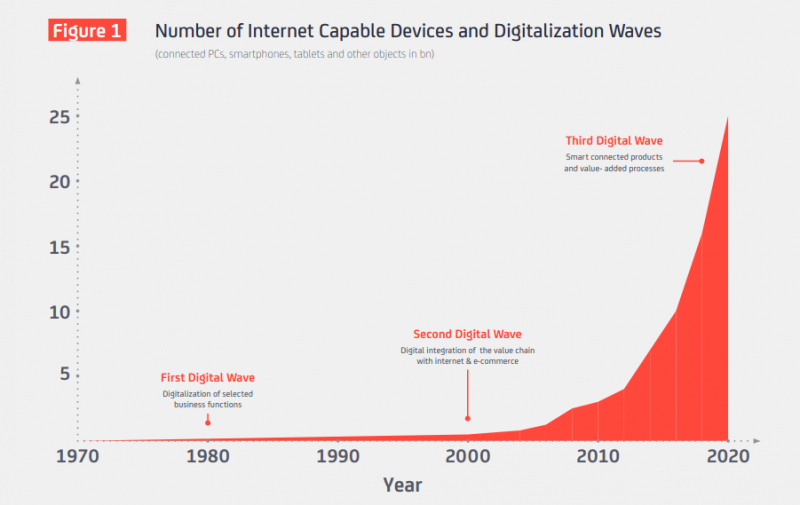
Information technology has been transforming the business environment in the last fifty years with digitalization and increasing numbers of connected devices. The “1st Wave” began with the introduction of PC’s and laptops within organizations. The IT focus then shifted increasingly cross-functional through the evolution of the internet and e-commerce. The emergence of smartphones led to the “2nd Wave” resulting in huge economic potential for early adopters and new innovative startups. The “3rd Wave” of digitalization driven by adoption of IoT which is expected to have an immense impact on personal life as well as on business firms.
Need for security
However, a lack of adherence to security guidelines while manufacturing IoT devices may hamper the embedded security for the Internet of Things market growth. Further, rising inclination toward cloud-based IoT platform security solutions which provides an in-built security framework is also influences the growth of the embedded security for Internet of things market.
Brute Force attack
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found.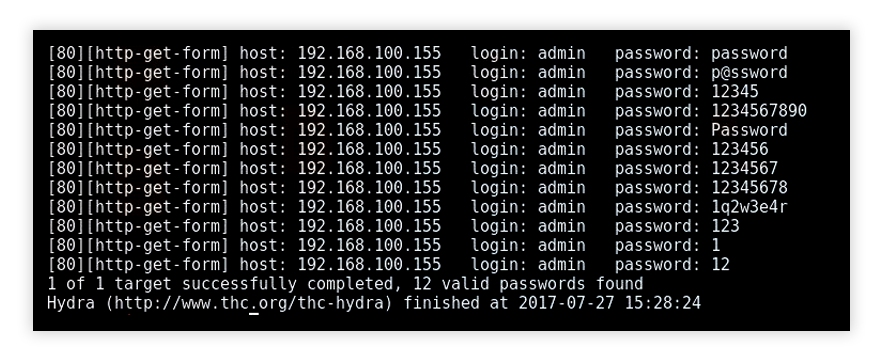 Security researchers have discovered a new malware called Kaji which is targeting IoT devices using SSH brute-force attacks. The malware is thought to be Chinese in origin and has stood out for its use of the programming language Go. The researchers believe Kaji is still a work-in-progress as it lacks features common in more advanced malware, contains the string “demo” in various places, and often crashes due to calling itself too many times and causing the host device to run out of memory. The malware only targets the root account of devices in order to have the ability to manipulate packets for carrying out DDoS attacks.
Security researchers have discovered a new malware called Kaji which is targeting IoT devices using SSH brute-force attacks. The malware is thought to be Chinese in origin and has stood out for its use of the programming language Go. The researchers believe Kaji is still a work-in-progress as it lacks features common in more advanced malware, contains the string “demo” in various places, and often crashes due to calling itself too many times and causing the host device to run out of memory. The malware only targets the root account of devices in order to have the ability to manipulate packets for carrying out DDoS attacks.
Eavesdropping attack
An eavesdropping attack, also known as a sniffing or snooping attack, is a theft of information as it is transmitted over a network by a computer, smartphone, or another connected device. The attack takes advantage of unsecured network communications to access data as it is being sent or received by its user.
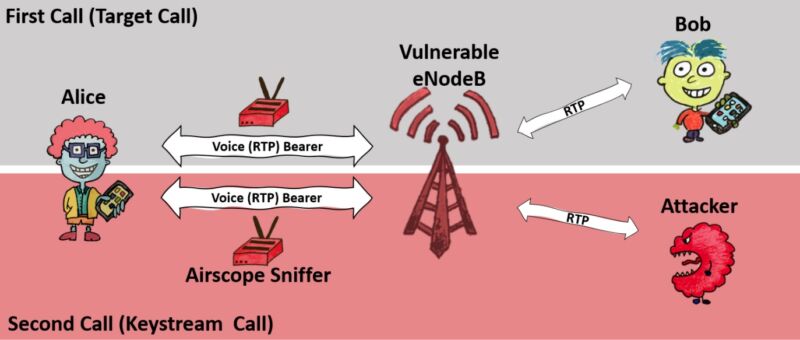
VoLTE encrypts call data as it passes between a phone and a base station. The base station then decrypts the traffic to allow it to be passed to any circuit-switched portion of a cellular network. The base station on the other end will then encrypt the call as it’s transmitted to the other party.
The implementation error ReVoLTE exploits is the tendency for base stations to use some of the same cryptographic material to encrypt two or more calls when they’re made in close succession. The attack seizes on this error by capturing the encrypted radio traffic of a target’s call, which the researchers call the target or first call. When the first call ends, the attacker quickly initiates what the researchers call a keystream call with the target and simultaneously sniffs the encrypted traffic and records the unencrypted sound, commonly known as plaintext.
Man in the Middle Attack
The man-in-the-middle concept is where an attacker attacks during IoT routing. Man-in-the-middle is a type of eavesdropping attack that occurs when a malicious actor inserts himself as a relay/proxy into a communication session between people or systems. A MITM attack exploits the real-time processing of transactions, conversations or transfer of other data.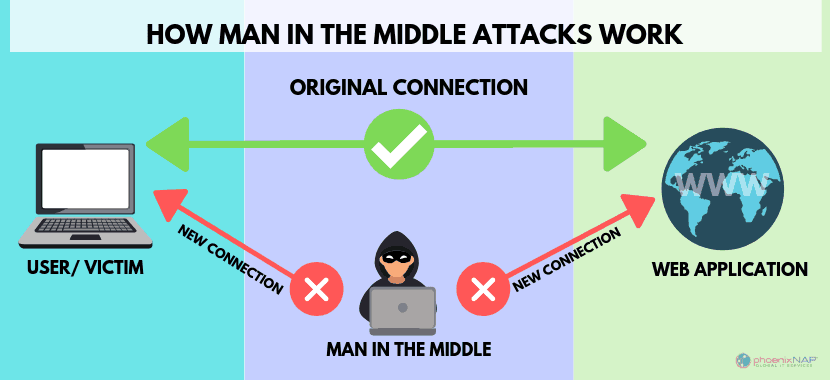
The bugs are found in the Asus RT-AC1900P whole-home Wi-Fi model, within the router’s firmware update functionality. The router uses GNU wget to fetch firmware updates from ASUS servers. It’s possible to log in via SSH and use the Linux/Unix “grep” command to search through the filesystem for a specific string that indicates that the vulnerability is present: “–no-check-certificate.”An attacker would need to be connected to the vulnerable router to perform a man in the middle attack (MITM), which would allow that person complete access to all traffic going through the device.
Botnet Attack
A botnet is a number of Internet-connected devices, each of which is running one or more bots. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allows the attacker to access the device and its connection.
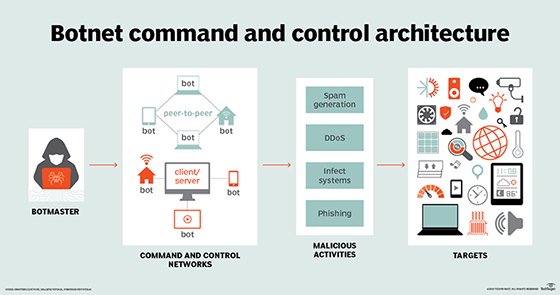 FritzFrog, which executes a worm malware written in Golang, was unearthed by a team at Guardicore. The malware deployed by the botnet is multi-threaded and fileless and disconcertingly leaves no trace on the disks of the machines it infects.It creates a backdoor in the form of an SSH public key, providing the attackers with ongoing access to victim machines. Organizations in the government, education, and finance industries have all been targeted by the botnet, which has managed to successfully breach over 500 servers. Victims include a railway company and universities in the United States and Europe.
FritzFrog, which executes a worm malware written in Golang, was unearthed by a team at Guardicore. The malware deployed by the botnet is multi-threaded and fileless and disconcertingly leaves no trace on the disks of the machines it infects.It creates a backdoor in the form of an SSH public key, providing the attackers with ongoing access to victim machines. Organizations in the government, education, and finance industries have all been targeted by the botnet, which has managed to successfully breach over 500 servers. Victims include a railway company and universities in the United States and Europe.
Social engineering
Social engineering is the act of manipulating people so they give up secret information. At its core, social engineering occurs when hackers manipulate your employees into compromising corporate security. Employees unwittingly reveal sensitive digital information needed to bypass network security such as passwords, or in physical scenarios unlock office doors for strangers, or hold them open to be polite, without checking someone has appropriate access and identification.
 The recent attack on Twitter that resulted in the takeover of numerous high-profile accounts including but not limited to those of President Barack Obama, Kanye West, and Tesla CEO Elon Musk, has brought to the fore the issue of social engineering once more.
The recent attack on Twitter that resulted in the takeover of numerous high-profile accounts including but not limited to those of President Barack Obama, Kanye West, and Tesla CEO Elon Musk, has brought to the fore the issue of social engineering once more.
Flaws in Hardware modules
Hardware security is a vulnerability protection that comes in the form of a physical device rather than software that is installed on the hardware of a computer system. Hardware security can pertain to a device used to scan a system or monitor network traffic. Common examples include hardware firewalls and proxy servers.A security flaw in a series of IoT connectivity chips could leave billions of industrial, commercial, and medical devices open to attackers.
 EHS8 modules are built for industrial IoT machines that operate in factories, the energy sector, and medical roles, and are designed to create secure communication channels over 3G and 4G networks. EHS8 modules host a lot of sensitive information: Passwords, encryption keys, and certificates are all commonly trusted to EHS8 modules to enable communication. A flaw in the chip was discovered by IBM’s X-Force Red hacking team. An attacker that manages to break in using IBM’s method could potentially control a device or gain access to the central control network to conduct widespread attacks – even remotely via 3G in some cases. Medical devices that an attacker penetrates could be manipulated to cover up concerning vital signs, create false panic situations, overdose patients, or cut off essential life-saving functions.
EHS8 modules are built for industrial IoT machines that operate in factories, the energy sector, and medical roles, and are designed to create secure communication channels over 3G and 4G networks. EHS8 modules host a lot of sensitive information: Passwords, encryption keys, and certificates are all commonly trusted to EHS8 modules to enable communication. A flaw in the chip was discovered by IBM’s X-Force Red hacking team. An attacker that manages to break in using IBM’s method could potentially control a device or gain access to the central control network to conduct widespread attacks – even remotely via 3G in some cases. Medical devices that an attacker penetrates could be manipulated to cover up concerning vital signs, create false panic situations, overdose patients, or cut off essential life-saving functions.
Wormhole Attack
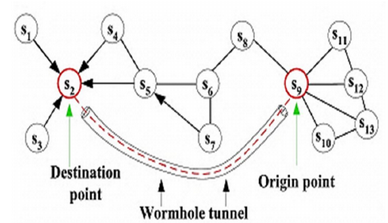
Wormhole attack is a grave attack in which two attackers locate themselves strategically in the network. Then the attackers keep on listening to the network, and record the wireless information. In wormhole attacks, the attacker receives packets at one point in the network and tunnels them to another part of the network and replays them into the network from that point onward.
 Providing security in IoT is challenging as the devices are resource constrained, the communication links are lossy, and the devices use a set of novel IoT technologies such as RPL and 6LoWPAN. Due to this it is easy to attack in IoT network.
Providing security in IoT is challenging as the devices are resource constrained, the communication links are lossy, and the devices use a set of novel IoT technologies such as RPL and 6LoWPAN. Due to this it is easy to attack in IoT network.
Injection attacks
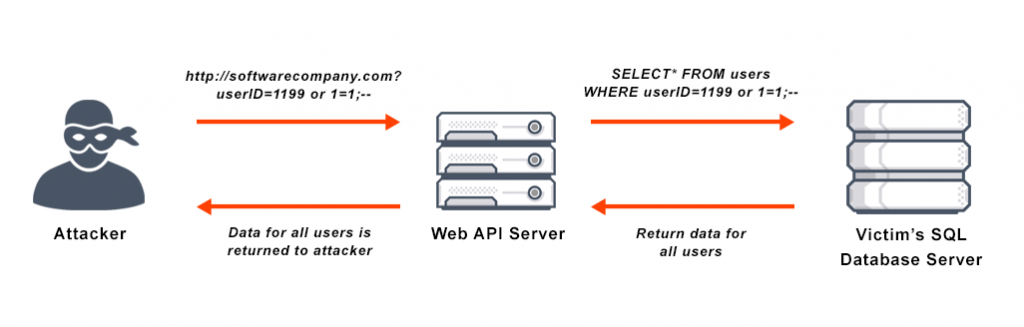
Injection attacks refer to a broad class of attack vectors that allow an attacker to supply untrusted input to a program, which gets processed by an interpreter as part of a command or query which alters the course of execution of that program. Injection attacks are amongst the oldest and most dangerous web application attacks. They can result in data theft, data loss, loss of data integrity, denial of service, as well as full system compromise.
During the process of transposing data transmitted between two objects equipped with NFC protocol, an attacker could insert some data into this data only, if the object needs a long time to reply. The wellturned insertion could only happen if the inserted data can be conveyed, before the original device starts with the answer. If both data streams overlap, the data will be unserviceable.
Conclusion
Cyber attack is an offensive and punishable strategy that could result in data loss, bankruptcy and misuse of drones, robots may even result in death. In this articles we have discussed about various types of attacks. In the next article, we will see what makes the devices vulnerable and how to mitigate them.