Cyber Security
What is Cyber security
Protecting internet-connected systems such as computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks
Cyber refers to the technology that includes systems, networks, programs, and data
security is concerned with the protection of systems, networks, applications, and information
electronic information security or information technology security.
"Cyber Security is the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, theft, damage, modification or unauthorized access. “
"Cyber Security is the set of principles and practices designed to protect our computing resources and online information against threats."
Types of Cyber Security
- Network Security
- Application Security
- Information or Data Security
- Identity management
- Operational Security
- Mobile Security
- Cloud Security
- Disaster Recovery and Business Continuity Planning
- User Education
Importance of Cyber Security
- Intellectual property, financial data, and personal data, can be sensitive for unauthorized access or exposure that could have negative consequences.
- we live in a digital era where all aspects of our lives depend on the network, computer and other electronic devices, and software applications.
- Cyber-attack is now an international concern that hacks the system, and other security attacks could endanger the global economy.
Cyber Security Goals
- Objective is to ensure data protection.
- Security community provides a triangle of three related principles to protect the data from cyber-attacks. This principle is called the CIA triad.
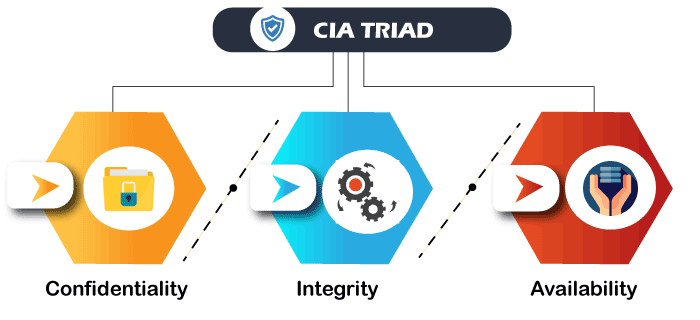
- Confidentiality
Data encryption is an excellent example of ensuring confidentiality.
- Integrity
This principle ensures that the data is authentic, accurate, and safeguarded from unauthorized modification by threat actors or accidental user modification.
If any modifications occur, certain measures should be taken to protect the sensitive data from corruption or loss and speedily recover from such an event.
It indicates to make the source of information genuine.
- Availability
This principle makes the information to be available and useful for its authorized people always
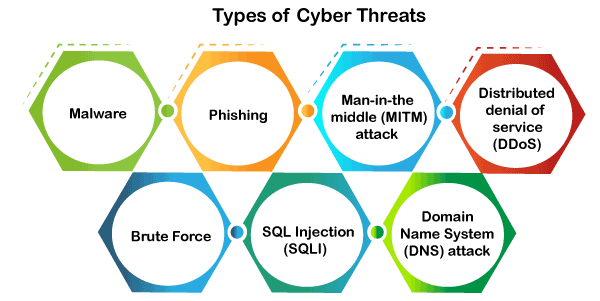
Types of Cyber Security Threats
- Virus
- Spyware
- Trojans
- Ransomware
- Worms
- Adware
- Botnets
Phishing
- sender seems to come from a genuine organization like PayPal, eBay, financial institutions, or friends and co-workers.
Man-in-the-middle (MITM) attack
- Cybercriminal intercepts a conversation or data transfer between two individuals.
Distributed denial of service (DDoS)
- Malicious attempt where cybercriminals disrupt targeted servers, services, or network's regular traffic
Brute Force
- cryptographic hack that uses a trial-and-error method
SQL Injection (SQLI)
- cybercriminals use malicious SQL scripts for backend database manipulation to access sensitive information.
Domain Name System (DNS) attack
- Redirect site users to malicious websites (DNS hijacking) and steal data from affected computers.
Benefits of Cyber Security
- Cyberattacks and data breach protection for businesses.
- Data and network security are both protected.
- Unauthorized user access is avoided.
- After a breach, there is a faster recovery time.
- End-user and endpoint device protection.
- Regulatory adherence.
- Continuity of operations.
- Developers, partners, consumers, stakeholders, and workers have more faith in the company's reputation and trust.
Cyber Safety Tips
- Conduct cybersecurity training and awareness
- Update software and operating system
- Use anti-virus software
- Perform periodic security reviews
- Use strong passwords
- Do not open email attachments from unknown senders
- Avoid using unsecured Wi-Fi networks in public places:
- Backup data
News
India reported 1,787 cyber-attacks a week on average in an organization in the last six months, as compared to the global average of 983
The cybersecurity threat landscape in India is getting wider, and the most attacked industry segment in India is the healthcare industry, followed by defense and education sectors, told the Hindu BusinessLine.
The top three vulnerable industry segments have something in common – a hybrid infrastructure, on-premises and cloud
.PNG)
.PNG)
 Neuralink
Neuralink  Cyber Security
Cyber Security  Ngrok
Ngrok 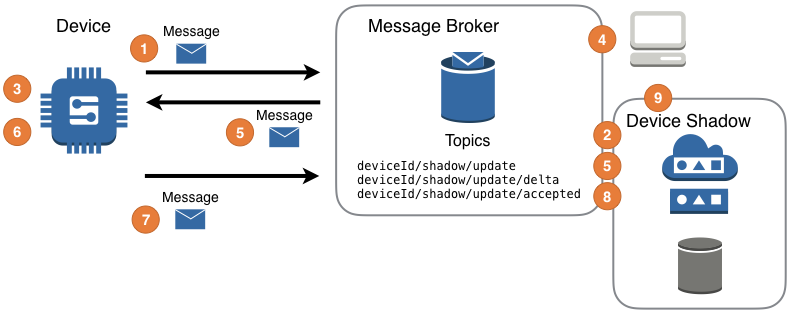 Exploring AWS IoT Device Shadow
Exploring AWS IoT Device Shadow