Ramarson Blogs and Update
IoT : Security measures and best practices
In the previous articles we have discussed about the various types of attacks that can happen on an IoT device. In this article, we will discuss about the security measures laid out by the OWASP (Open Web Application Security Project ). The OWASP top 10 IoT vulnerabilities list is a resource fRead more...
Cyber attacks on IoT devices
VoLTE encrypts call data as it passes between a phone and a base station. The base station then decrypts the traffic to allow it to be passed to any circuit-switched portion of a cellular network. The base station on the other end will then encrypt the call as it’s transmitted to the otRead more...
RAMARSON-10th Year of Passion
Sharing the Journery of Ramarson`s 9 complete years of industrial experiences with all joy as we are entering into 10th year of passion and excellence.Read more...
Every Software Developers Should know
Consistent learning and Updating why is it so? The fast-moving tech industry demands updated technologies to implement as fast as it can be The reason is the efficiency and&nbRead more...
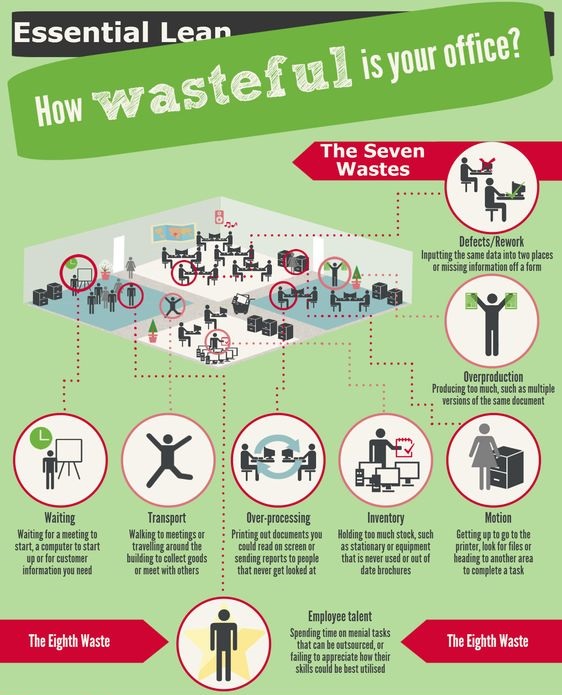
ESSENTIAL LEAN
Introduction : I wish to share this which I read through an image shared on Pinterest byRead more...
WELCOME MESSGAE
Dear Ramarson Experts, I welcome you all for this new beginning. I request all the team members to contribute for the blog and share your valuable thoughts, ideas and experience to the world. Lets encourage intellectual discussion and use this platform to share knowledge. YouRead more...

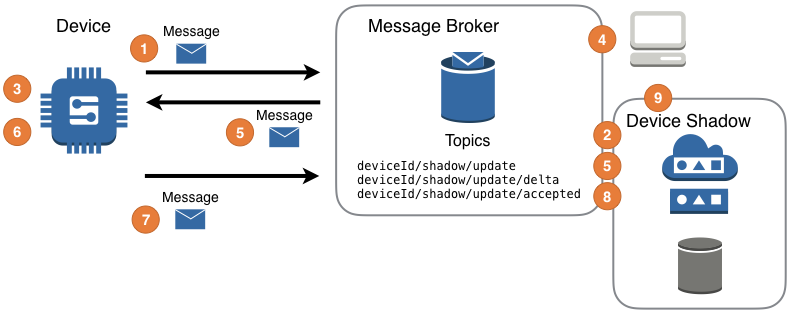

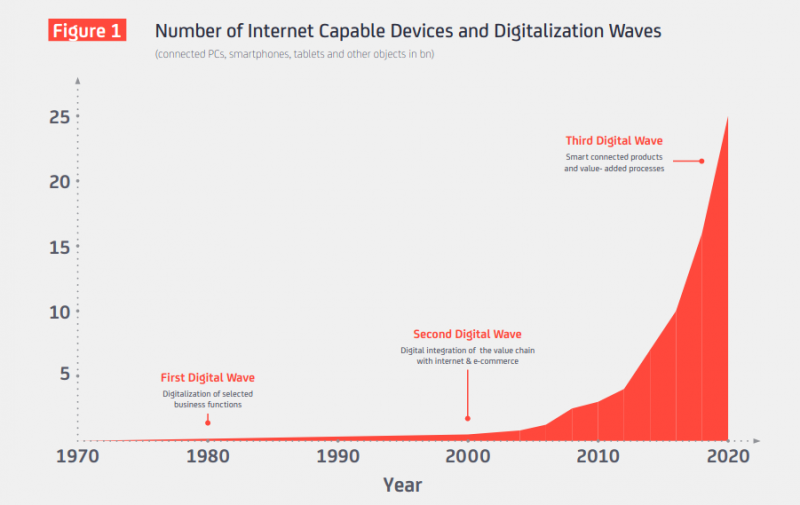





 Neuralink
Neuralink  Ngrok
Ngrok